1. Inventory Your Accounts
Commence with a meticulous audit of your social media landscape. Many individuals discover they have accounts on platforms they no longer use. Utilizing a tool or manually searching your email for account creation confirmations can aid in compiling a comprehensive list. This inventory will serve as the foundation for your cleanup efforts.
2. Tighten Privacy Settings
Each social media platform offers privacy settings, often buried within user interfaces. Delve into these settings and adjust them to minimize public visibility. Opt for the most restrictive settings that still allow you to enjoy the platform’s social aspects. This action significantly reduces your exposure to unwanted scrutiny and data harvesting.
3. Curate Your Connections
Social media is predicated on connections, yet not all are beneficial or desired. Scrutinize your friend lists and follower connections, removing those that are superfluous or unknown. This curation process streamlines your social media interactions and mitigates the risk of information exposure to potentially malicious actors.
- Inventory Your Accounts: Begin with a comprehensive audit of all your social media accounts, including those you may need to remember.
- Tighten Privacy Settings: Adjust your privacy settings on each platform to limit who can see your information and posts.
- Curate Your Connections: Evaluate your friend lists and follower counts, removing unnecessary or unknown connections.
- Eliminate Sensitive Content: Scrutinize your profiles for any sensitive or personal information that might be publicly visible and remove it.
- Deactivate or Delete Old Accounts: Consider whether old, unused accounts should be temporarily deactivated or deleted permanently for security reasons.
- Update Security Measures: Strengthen your accounts by updating passwords and enabling two-factor authentication wherever possible.
- Review App Permissions: Audit third-party app permissions to ensure they don’t have unnecessary access to your social media accounts.
- Implement a Continuous Monitoring Strategy: Develop a routine for regularly checking and updating your social media settings and security measures.
- Educate Yourself on the Latest Privacy Features and Threats: To maintain a secure online presence, stay informed about new privacy settings and potential cybersecurity threats.
4. Eliminate Sensitive Content
Over time, one might inadvertently share sensitive personal information or content that cybercriminals could exploit. Conduct a thorough review of your posts, comments, and shared media, removing anything that could compromise your privacy or security. This includes geolocation tags, personally identifiable information, and content not aligning with your professional image.
5. Deactivate or Delete Old Accounts
Dormant accounts are a cybersecurity liability. They can become targets for hackers and act as a backdoor to your digital life. Decide whether to deactivate or permanently delete these profiles. Deactivation is reversible, allowing you to retain your data, while deletion is a definitive severance from the platform.
6. Update Security Measures
Enhance your accounts’ security by updating passwords and enabling two-factor authentication (2FA) where available. Create unique, complex passwords for each platform to impede unauthorized access. Consider utilizing a password manager to manage these credentials efficiently.
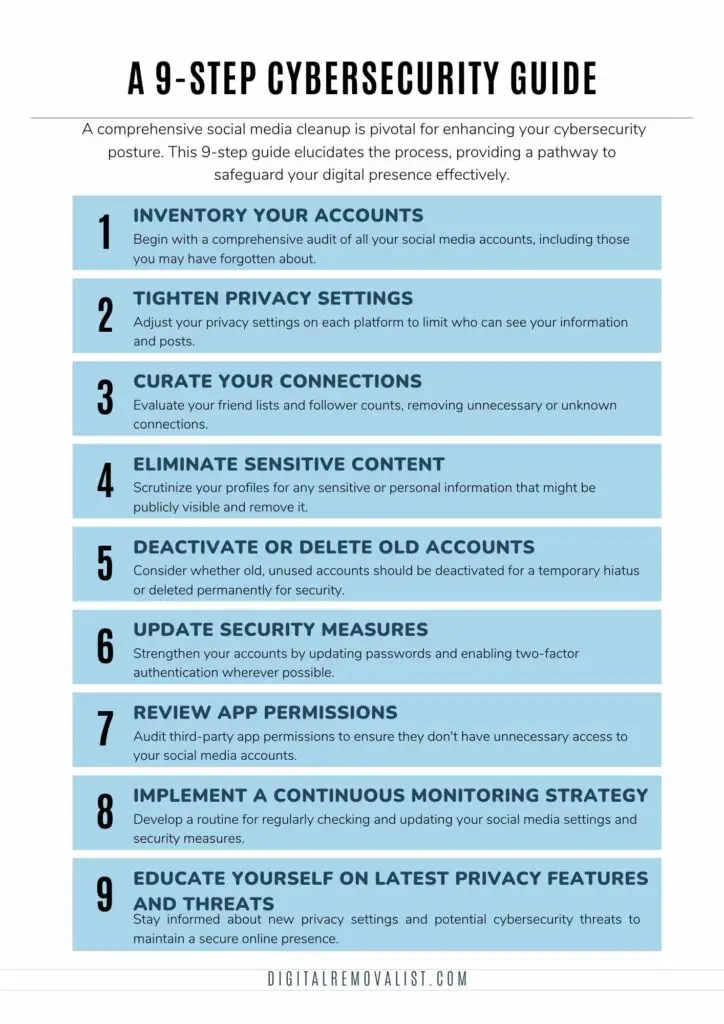
7. Review App Permissions
Many social media accounts are interconnected with third-party applications, granting them varying access to your data. Review these permissions critically, revoking access to apps that are no longer in use or appear suspicious. This step prevents these external entities from gleaning more information than necessary.
8. Implement a Continuous Monitoring Strategy
Cybersecurity is not a one-off task but a continuous commitment. Establish a routine for regularly reviewing your social media settings, connections, and shared content. Staying vigilant and proactive is critical to mitigating potential risks and ensuring digital well-being.
9. Educate Yourself on Latest Privacy Features and Threats
Stay abreast of the latest developments in social media privacy features and cybersecurity threats. Platforms frequently update their settings and policies, offering new tools to protect your privacy. Simultaneously, cyber threats evolve, necessitating an ongoing effort to educate oneself to navigate these challenges adeptly.
Conclusion
A social media cleanup is a critical component of modern digital hygiene. Following this 9-step guide can significantly enhance your cybersecurity posture, protecting yourself against potential threats and ensuring your private information remains secure. Remember, the digital realm is perpetually evolving, and so should our strategies to defend our presence.







